Securing your Azure Environment
2024年3月22日- By Hisham Nawzer
The cloud offers undeniable benefits, but security remains a paramount concern. Securing your Azure environment requires a comprehensive strategy. This involves managing user access, safeguarding sensitive data, and adhering to other security best practices. This article will explore how you can secure Azure environment by implementing strong identity and access controls.

Implementing Identity and Access Management (IAM)
Identity and Access Management (IAM) in Azure refers to the framework and set of tools provided by Microsoft to manage user identities and control access to Azure resources. IAM enables organizations to securely authenticate, authorize, and manage access for users, applications, and services within their Azure environment.
Use of RBAC in IAM
RBAC, or Role-Based Access Control, is a fundamental component of Identity and Access Management (IAM) in Azure. It provides a granular way to manage access to Azure resources by assigning roles to users, groups, or applications. RBAC allows you to control what actions users can perform and what resources they can access within Azure.
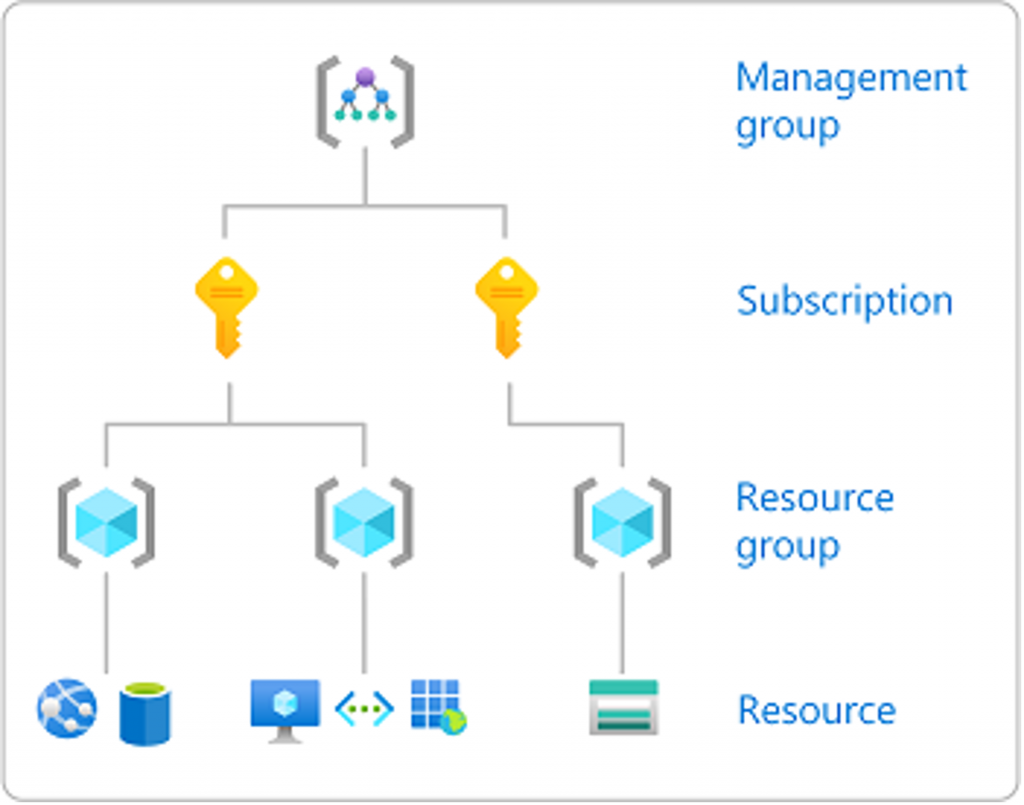
Key Aspects of RBAC in Azure IAM
Roles: Azure provides a set of built-in roles with predefined sets of permissions, such as Owner, Contributor, and Reader. These roles encompass a range of actions that users can perform on Azure resources[1]. Additionally, you can create custom roles tailored to your specific organizational requirements.
Role Assignments: Role assignments associate users, groups, or applications with specific roles, granting them the permissions associated with those roles. Role assignments can be applied at different scopes, including Management group, subscriptions, resource groups, and individual resources[2]
Scopes: RBAC operates within a hierarchical structure of scopes, which includes subscriptions, resource groups, and individual resources. Role assignments made at higher levels of the hierarchy are inherited by lower levels, providing a consistent access control mechanism.
Access Control Policies: Access control policies define the permissions that are granted to security principals (users, groups, or applications) at specific scopes. These policies are used to enforce RBAC and govern access to resources within Azure.
RBAC in Azure IAM enables organizations to implement least privilege principles, ensuring that users have only the permissions necessary to perform their job functions. By leveraging RBAC, organizations can strengthen security, streamline access management, and maintain compliance with regulatory requirements.
RBAC enables organizations to implement the principle of least privilege, ensuring that users have only the permissions necessary to perform their job functions. By centralizing access management and enforcing access policies based on roles, RBAC helps enhance security, streamline access control, and maintain compliance with regulatory requirements in Azure environments.
Azure Cost Optimization Free Assessment
Need help with the first step in achieving cost optimization for your Microsoft Azure environment? iret’s Global Solutions Division offers a free of charge assessment of Microsoft Azure environment for corporate organizations located in Japan. Our expert level Azure engineers will examine your Azure infrastructure to identify existing or potential causes for increasing costs. We will provide the research outcome as a report with suggestions for specific actions – at no cost. We also invite you to a briefing by the engineers to help you understand the report. To learn more about the campaign, please feel free to contact the Global Solutions Division via this special site. (Japanese language site; Campaign is offered in English and Japanese)
About Rackspace
Discover the power of Rackspace Technology, brought to you by the Global Solutions Division of Iret Inc. in Japan. Elevate your cloud experience with our tailored end-to-end AWS and Microsoft Azure solutions. From expert consulting and seamless integration to cutting-edge development and daily operations, we are your dedicated partner in unleashing the full potential of the cloud. Are you ready to get started? Click the contact button below to get in touch with one of our experts.